Preface
Tor stands for “The Onion Router”. Users who use Tor can browse online websites anonymously (relatively), chat, and send instant messages. The official project address is torproject
, and its corresponding onion domain name is http://2gzyxa5ihm7nsggfxnu52rck2vv4rvmdlkiu3zzui5du4xyclen53wid.onion/
. The onion domain name can only be accessed through Tor Browser.
This article mainly introduces the process of building an onion site for technical exchange.
Set Up Nginx server
Because there is a conflict between Tor’s forwarding and Caddy’s automatic https processing, we use Nginx as the static server for the Hugo site. The configuration is as follows:
server {
listen 127.0.0.1:8080;
port_in_redirect off;
root /var/www/tomo.dev;
index index.html;
server_name _;
location / {
# First attempt to serve request as file, then
# as directory, then fall back to displaying a 404.
try_files $uri $uri/ =404;
}
error_page 404 /404.html;
}
Among them, port_in_redirect is used to turn off the port 8080 brought in the jump, otherwise, when requesting paths like /posts, it will jump to :8080/posts/. If Nginx listens on port 80, you don’t need to set this parameter. After the setup, you can test whether the site access is normal by using the command curl http://127.0.0.1:8080 on the server.
Install and configure Tor
The server uses Ubuntu, and you need to add the tor repository source:
sudo apt install apt-transport-https
# add the gpg key
wget -qO- https://deb.torproject.org/torproject.org/A3C4F0F979CAA22CDBA8F512EE8CBC9E886DDD89.asc | gpg --dearmor | sudo tee /usr/share/keyrings/tor-archive-keyring.gpg >/dev/null
# add apt repository
echo "deb [signed-by=/usr/share/keyrings/tor-archive-keyring.gpg] https://deb.torproject.org/torproject.org $(lsb_release -cs) main" | sudo tee -a /etc/apt/sources.list.d/tor.list
echo "deb-src [signed-by=/usr/share/keyrings/tor-archive-keyring.gpg] https://deb.torproject.org/torproject.org $(lsb_release -cs) main" | sudo tee -a /etc/apt/sources.list.d/tor.list
# install
sudo apt update
sudo apt install tor deb.torproject.org-keyring
After installation, we configure Tor. Its configuration file is /etc/tor/torrc. The main configurations are the following two items:
HiddenServiceDir /var/lib/tor/tomo.dev/
HiddenServicePort 80 127.0.0.1:8080
Among them, HiddenServiceDir indicates the directory where site information and keys are stored after running, and HiddenServicePort declares a virtual port and a forwarding port. The above configuration indicates that the site information is in the directory /var/lib/tor/tomo.dev/, and the site listens on port 80 and forwards it to the local port 8080 (that is, the Nginx server port configured before).
After configuration, we restart the Tor service sudo systemctl restart tor.service. If successful, we can see the following files in the /var/lib/tor/tomo.dev/ directory:
ll /var/lib/tor/tomo.dev/
total 24
drwx--S--- 3 debian-tor debian-tor 4096 Mar 22 01:15 ./
drwx--S--- 4 debian-tor debian-tor 4096 Apr 7 10:54 ../
drwx--S--- 2 debian-tor debian-tor 4096 Mar 22 01:15 authorized_clients/
-rw------- 1 debian-tor debian-tor 63 Mar 22 01:15 hostname
-rw------- 1 debian-tor debian-tor 64 Mar 22 01:15 hs_ed25519_public_key
-rw------- 1 debian-tor debian-tor 96 Mar 22 01:15 hs_ed25519_secret_ke
Among them, hostname is the domain name of our onion site
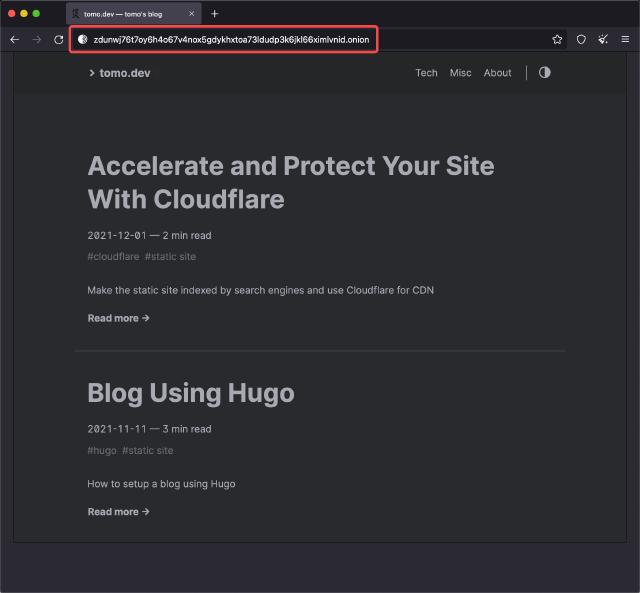
cat hostname
zdunwj76t7oy6h4o67v4nox5gdykhxtoa73ldudp3k6jkl66ximlvnid.onion
Enter this address in the Tor browser and try to access it. If the network is reachable and the configuration is correct, you will see the following page:
Follow-up
The hostname of the Onion site is generated from the public key. The length of the V3 version of the site is 56. If we want a more personalized site name (such as duckduckgo’s onion site is https://duckduckgogg42xjoc72x3sjasowoarfbgcmvfimaftt6twagswzczad.onion The prefix is duckduckgo), you can use tools to generate it. The longer the length of the customized prefix is required, the longer the generation time will be (similar to hash collision). The following table is the approximate time required to generate a specific length prefix (1.5GHz processor, reference ):
| Characters | Time |
|---|---|
| 1 | Less than 1 second |
| 2 | Less than 1 second |
| 3 | Less than 1 second |
| 4 | 2 seconds |
| 5 | 1 minute |
| 6 | 30 minutes |
| 7 | 1 day |
| 8 | 25 days |
| 9 | 2.5 years |
| 10 | 40 years |
| 11 | 640 years |
| 12 | 10 millennia |
| 13 | 160 millennia |
| 14 | 2.6 million years |
We can use the tool mkp224o to generate:
git clone https://github.com/cathugger/mkp224o.git
cd mkp224o
./autogen.sh
./configure --enable-amd64-51-30k
make
Specific compilation parameters can be viewed in the official README. After compilation, you can use ./mkp224o --help to view the usage parameters. Currently, use ./mkp224o -d ~/onion -n 1 -s tomodev to generate our site name with the prefix tomodev. The output during the running process is as follows:
./mkp224o -d ~/onion -n 1 -s tomodev
set workdir: /home/tomo/onion/
sorting filters... done.
filters:
tomodev
in total, 1 filter
using 8 threads
>calc/sec:15309395.081099, succ/sec:0.000000, rest/sec:79.949632, elapsed:0.100063sec
>calc/sec:16125412.147448, succ/sec:0.000000, rest/sec:0.000000, elapsed:10.106494sec
>calc/sec:16116784.889587, succ/sec:0.000000, rest/sec:0.000000, elapsed:20.112309sec
...
>calc/sec:14133147.405534, succ/sec:0.000000, rest/sec:0.000000, elapsed:4770.152169sec
>calc/sec:14011151.614585, succ/sec:0.000000, rest/sec:0.000000, elapsed:4780.157895sec
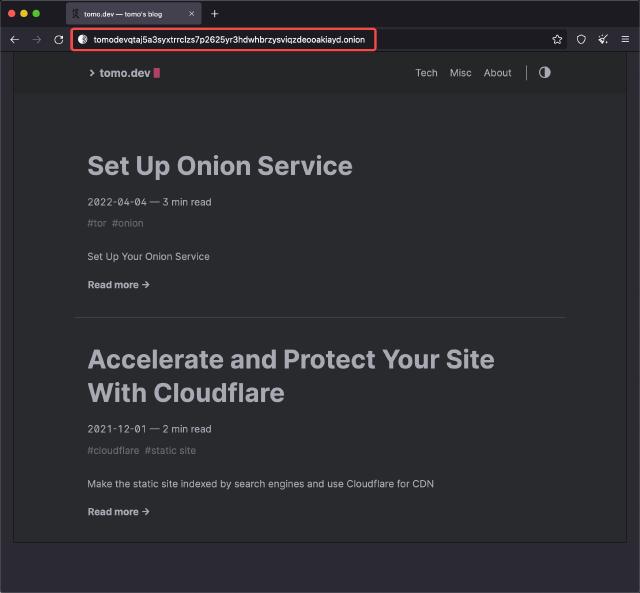
tomodevqtaj5a3syxtrrclzs7p2625yr3hdwhbrzysviqzdeooakiayd.onion
waiting for threads to finish... done.
It takes about 1.5 hours to run on an 8-core machine, and the results are saved in /home/tomo/onion/. View the contents of the hostname, and you can see the generated site name. Synchronize this directory to the server, replacing the contents of the previous directory.
Restart the tor service, we can visit the Tor browser for testing, the results are as follows: